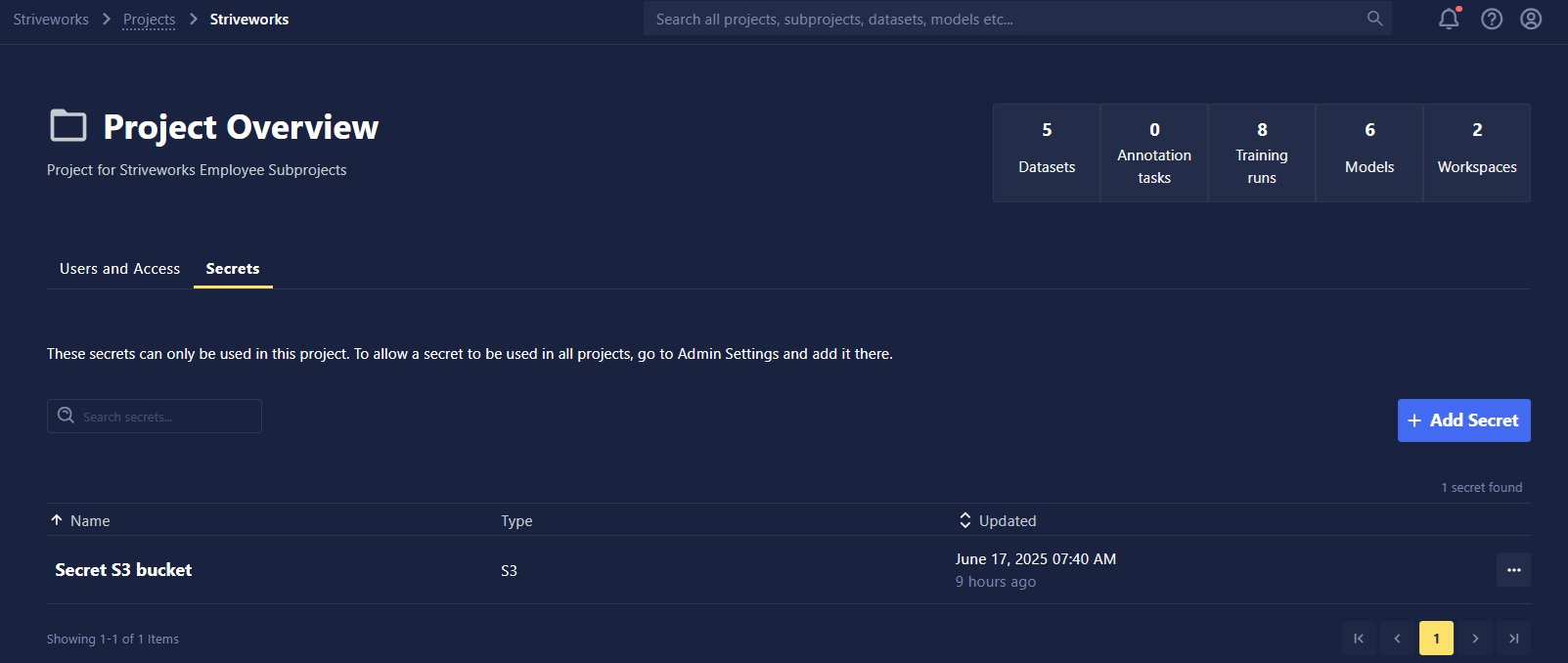
Secrets
Secrets provide secure storage and management of sensitive information such as API keys, passwords, tokens, and certificates. These are essential for protecting access to external services, databases, and internal systems.
What Are Secrets?
Secrets in Chariot allow you to securely store sensitive data that your models, Training Runs, and other processes need to access external resources. By using Secrets, you avoid hardcoding sensitive information in your code or configuration files.
Secrets in Chariot are associated with, and owned by, either a project or an organization. At the moment, all Secrets created via the Chariot user interface are project-level Secrets.
Creating Secrets
To create a Secret:
- Navigate to a project of your choice and click the Secrets tab.
- Click +Add Secret.
- Follow the wizard to create a Secret.
Users who have Read access to this project will be able to view the Secret's existence but not the values. Users with Write and Owner permission can create Secrets, view the Secret values themselves, and modify the values for the Secret. For more on permissions, see Roles & Permissions.
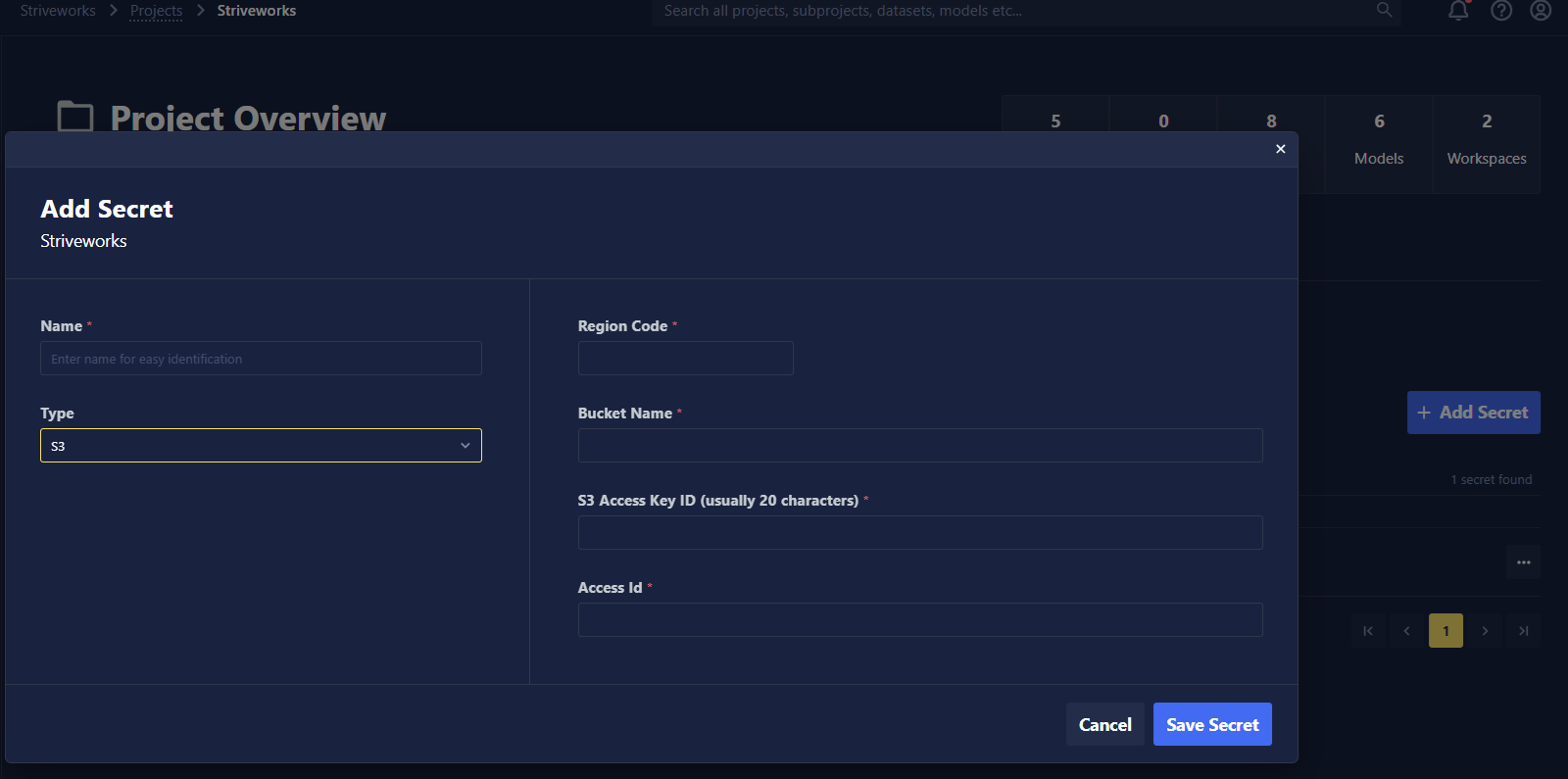
Types of Secrets
- Single Variable: For individual values like API keys, passwords, tokens, etc.
- S3 Connection: For AWS S3 access credentials.
- Container Registry: Specifies a registry server and a valid username and password.
- An example of how to use Container Registry Secrets with Training Blueprints can be found here.
Accessing Secrets
You can access Secrets through the API. This can be helpful if you want to reference the Secrets within a Workspace. To use the API, set your authorization header so that it contains bearer [your-token], which can be found on your profile or obtained from the Chariot SDK using the client.get_bearer_token function.
The following API request will list all of the Secrets for that project:
GET https://%%CHARIOT-HOST%%/api/identity/v2/settings/project/[project-id]/?sort=name&desc=false
You will get a payload that looks similar to the following JSON:
{
"data": [
{
"_id": "2kFmBSWjqxWEGarZC9kkeYOpgMD",
"_key": "secret/Custom/2kFmBSWjqxWEGarZC9kkeYOpgMD",
"_type": "secret/Custom",
"_updated_at": 1722887562,
"name": "test",
"value": "********"
}
]
}
To retrieve the actual content of a Secret, you will need the _key. Note that the ?decrypt=true query parameter is needed to get the real value out of the Secret. Only people with Write access will get a response from this API call:
GET https://%%CHARIOT-HOST%%/api/identity/v2/settings/project/[project-id]/[key]?decrypt=true
For more details, see the Settings (v2) Swagger API docs at:
https://%%CHARIOT-HOST%%/api/identity/v1/swagger/index.html
Best Practices
- Use Secrets for all sensitive data.
- Rotate Secrets regularly.
- Remove unused Secrets.